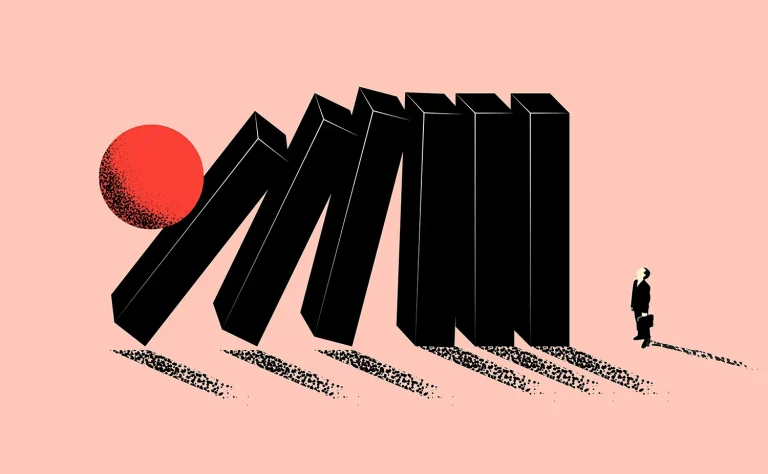
Most cloud breaches are not the result of “hacking” in the traditional sense; they are the result of misconfiguration. Our Security Operations Center (SOC) operates on the principle of proactive defense.

Identity and Access Management (IAM)
Multi-Factor Authentication (MFA)
We enforce hardware-based MFA (like YubiKeys) or biometrics for all administrative access.
Principle of Least Privilege (PoLP)
No user is given more access than they absolutely need for their specific job function. This limits the "blast radius" in the event of a credential leak.
Just-In-Time (JIT) Access
For high-level system changes, we grant temporary permissions that expire automatically once the task is complete.
Why us
Continuous Compliance & Monitoring
Security is not a one-time setup; it is a 24/7/365 marathon.
AI-Powered Threat Detection: Our systems use behavioral analytics to identify “strange” behavior. If an employee who usually logs in from New York suddenly attempts a bulk data download from an IP address in a different country, the account is locked instantly.
Vulnerability Scanning: We run automated “Penetration Tests” daily to find and patch software vulnerabilities before they can be exploited.
DDoS Protection: Our massive bandwidth capacity and automated scrubbing centers can absorb and neutralize even the largest Distributed Denial of Service attacks, keeping your website online while others go dark.


Network Security & Micro-Segmentation
Isolated Workloads
We divide your cloud environment into small, isolated zones. A breach in a web server cannot "jump" to your database server because there is no internal path between them.
Web Application Firewalls (WAF)
We filter out malicious traffic, SQL injections, and Cross-Site Scripting (XSS) attacks before they ever reach your application.